Man-in-the-Middle Detection Tryhackme Answers
Dive into the interactive TryHackMe room focused on Man-in-the-Middle (MITM) detection, where you’ll deploy virtual machines, launch real-world ARP/DNS spoofing attacks, and use packet capture tools like Wireshark to spot and analyse malicious interceptions.
MITMINCIDENT RESPONSEMETHODOLOGYDETECTIONTOOLSDEFENDER XDRTRYHACKME WRITEUPSTECHNOLOGYSECURITYPENETRATION TESTINGPHISHINGCREDENTIAL DUMPINGTRYHACKME WALKTHROUGHNETWORK DISCOVERYNETWORKINGTHREAT DETECTIONINFORMATION SECURITY (INFOSEC)TRYHACKME ANSWERSETHICAL HACKINGCYBERSECURITYTRYHACKMEOPEN-SOURCE TOOLSVULNERABILITIESENCRYPTIONS
Jawstar
10/21/20251 min read

Task 4 : Detecting ARP Spoofing
How many ARP packets from the gateway MAC Address were observed?
10
What MAC address was used by the attacker to impersonate the gateway?
02:fe:fe:fe:55:55
How many Gratuitous ARP replies were observed for 192.168.10.1?
2
How many unique MAC addresses claimed the same IP (192.168.10.1)?
2
How many ARP spoofing packets were observed in total from the attacker?
14
Task 5 : Unmasking DNS Spoofing
How many DNS responses were observed for the domain corp-login.acme-corp.local?
211
How many DNS requests were observed from the IPs other than 8.8.8.8?
2
What IP did the attacker’s forged DNS response return for the domain?
192.168.10.55
Task 6 : Spotting SSL Stripping in Action
How many POST requests were observed for our domain corp-login.acme-corp.local?
1
What's the password of the victim found in the plaintext after successful ssl stripping attack.
Secret123!
Task 7 : Conclusion & Room Wrap-up
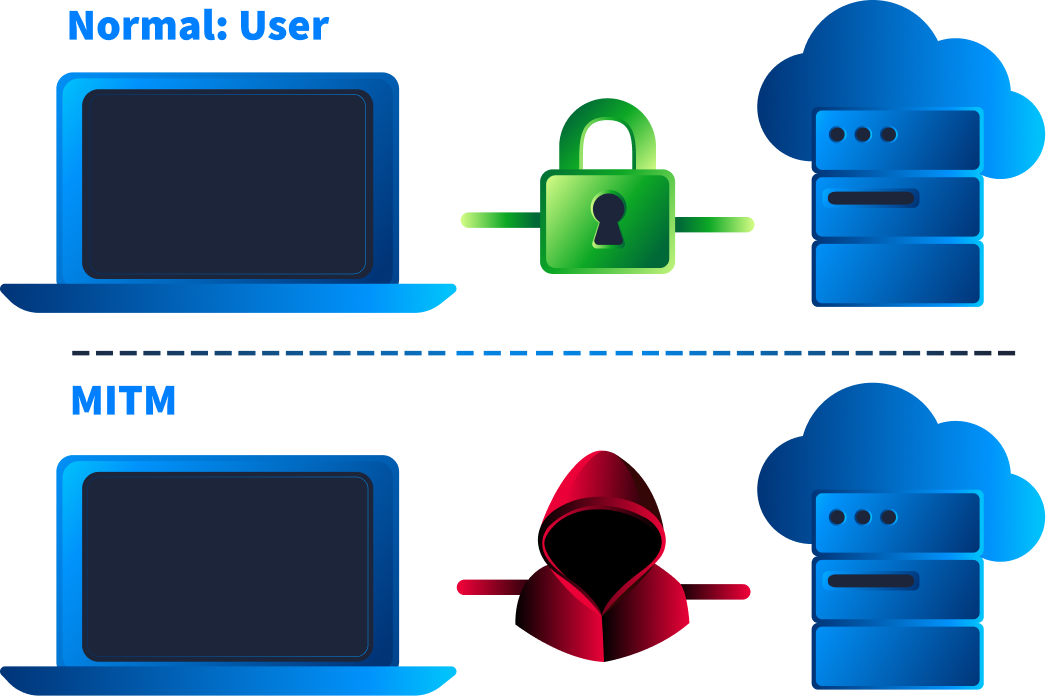
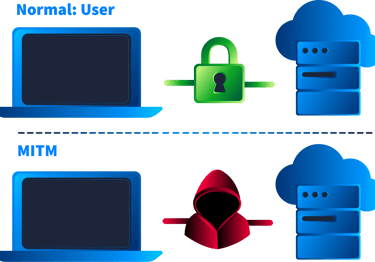
In this room, we explored some common man-in-the-middle attacks chained together in a scenario and how to identify the footprints in the network traffic.
Please note that similar logs are placed in the mitm_network logs folder and pre-ingested into Splunk for you to try.
Some of the key concepts covered in this room are:
Detected by finding duplicate MAC addresses for different IPs in the ARP cache (arp -a) or by spotting in Wireshark.
DNS Spoofing: Unmasked by finding multiple, conflicting DNS responses.
SSL Stripping: Exposed by finding sensitive data, like passwords, being sent in plaintext over HTTP to websites that should be secure.
Connect
Secure your future with expert cybersecurity solutions
Support
Quick Links
© 2025. All rights reserved.
contact@jawstarsec.in
