Network Traffic Basics Tryhackme Answers
Network Traffic Basics — hands-on intro to packet capture, TCP/UDP, and protocol analysis using Wireshark. Learn to inspect, filter, and troubleshoot network flows.
WIRELESSDETECTIONTOOLSTRYHACKME WRITEUPSPENETRATION TESTINGSECURITYTECHNOLOGYNETWORK DISCOVERYTRYHACKME WALKTHROUGHINTERNETNETWORKINGCYBERSECURITYTRYHACKMEOPEN-SOURCE TOOLSENCRYPTIONS
Jawstar
10/17/20252 min read
Task 1 : Introduction
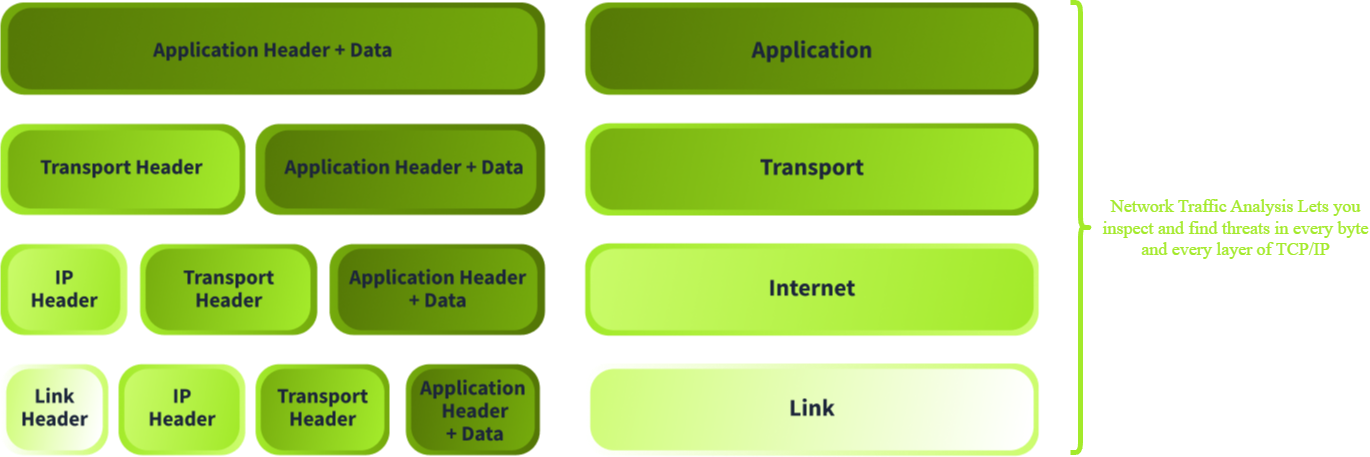
Network Traffic Analysis (NTA) is a process that encompasses capturing, inspecting, and analyzing data as it flows in a network. Its goal is to have complete visibility and understand what is communicated inside and outside the network. It is important to stress that NTA is not a synonym for the tool Wireshark. It is more than that: It is a combination of correlating several logs, deep packet inspection, and network flow statistics with specific outlined goals (which we will discuss later on).
Knowing how to analyze network traffic is an essential skill, not only for an aspiring SOC L1 analyst but also for many other blue and red team roles. As an L1 analyst, you need to be able to navigate through the sea of network information and understand what is normal and what deviates from the baseline.
In this room, we will focus on defining network traffic analysis, why you need it, what and how you can observe network traffic, and some of the sources and flows of network traffic you need to be aware of.
Learning Objectives
Know what network traffic analysis is
Know what can be observed
Know how to observe network traffic
Know typical network traffic sources and flows
Task 2 : What is the Purpose of Network Traffic Analysis?
What is the name of the technique used to smuggle C2 commands via DNS?
DNS Tunneling
Task 4 : What Network Traffic Can We Observe?
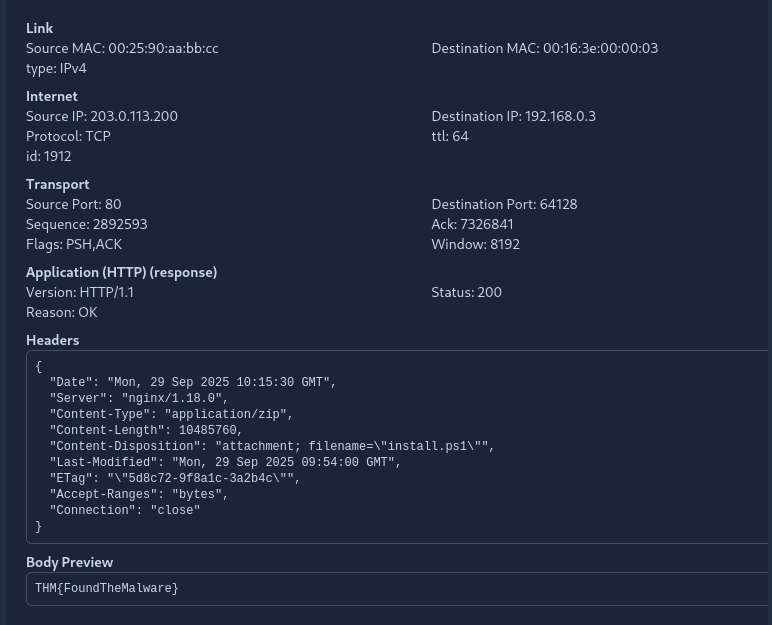
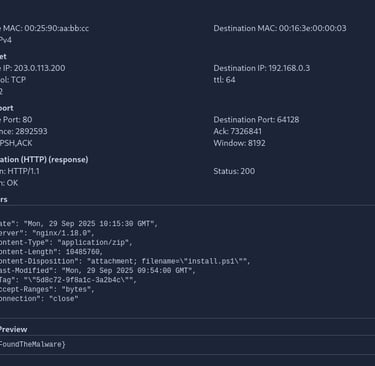
Look at the HTTP example in the task and answer the following question: What is the size of the ZIP attachment included in the HTTP response? Note down the answer in bytes.
10485760
Which attack do attackers use to try to evade an IDS?
Fragmentation
What field in the TCP header can we use to detect session hijacking?
Sequence Number
Task 3 : What Network Traffic Can We Observe?
Which category of devices generates the most traffic in a network?
Endpoint Devices
Before an SMB session can be established, which service needs to be contacted first for authentication?
kerberos
What does TLS stand for?
Transport Layer Security
Task 5 : How Can We Observe Network Traffic?
What is the flag found in the HTTP traffic in scenario 1?
Check the given image above
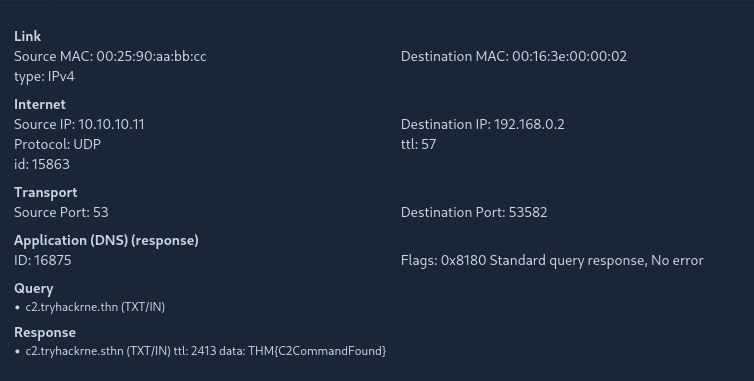
What is the flag found in the DNS traffic in scenario 2?
Check the given image above
Task 6 : Conclusion
Now that we know what NTA is, why we need it, how to capture network traffic and analyze it; we are ready to get hands on with effectively analyzing network traffic using a tool called Wireshark. Proceed to the next room to get started with the basics of Wireshark.
Subscribe to get more ............
Connect
Secure your future with expert cybersecurity solutions
Support
Quick Links
© 2025. All rights reserved.
contact@jawstarsec.in
